安装与简介
1 | $ git clone https://github.com/radare/radare2 |
这个软件的优势应该是开源,支持多架构,多系统
实践
rabin2
第一个工具rabin2,这个比readelf,file强大
1 | -I binary info |
查看binary的信息
1 | # rabin2 -I ./intro |
查看字符串
1 | -z strings (from data section) |
结果:
1 | # rabin2 -z ./intro |
当然查看更多可以下面这两个
1 | -zz strings (from raw bins [e bin.rawstr=1]) |
r2
这个应该是核心工具
启动:
1 | # r2 ./intro |
分析的话可以输入aa,如果想要更详细,可以aaa,或者aaaa
1 | # r2 ./intro |
分析完我们要去看函数,就用s,s代表就是seek,我们操作文件应该用过fseek
我们jmp到main函数
1 | [0x00000540]> s main |
可以看到前面的变了,前面的应该是偏移
当然我们也可以切换回来
1 | [0x0000064a]> s 0x540 |
但现在我们还是看不到代码,还是命令行,我们可以用v切换为显示模式,代表visual mode,有英文详细名词好记
我们输入v就看到了十六进制的界面了
我们这是可以再用p来切换其他模式,我们可以切花到下面的
1 | [0x0000064a 19% 512 ./intro]> pd $r @ main |
如果想后退按esc就行
实战一个crackme
先看一下信息
1 | # rabin2 -I ./crackme |
先运行
1 | # ./crackme |
我们之前用-z查看字符串,我们如果只查看字符串而不看地址什么的
1 | -qq show less info (no offset/size for -z for ex.) |
用-zqq可以显示更少信息
1 | rabin2 -zqq ./crackme |
我们可以猜想radare2就是password
1 | # ./crackme |
这就是最简单的,不过这还有第二个password呢
我们用r2看看吧
1 | # r2 ./crackme |
如果要切换到想ida那样的,就用VV,之后就可以用方向键控制了
我们就可以清晰看到password1了
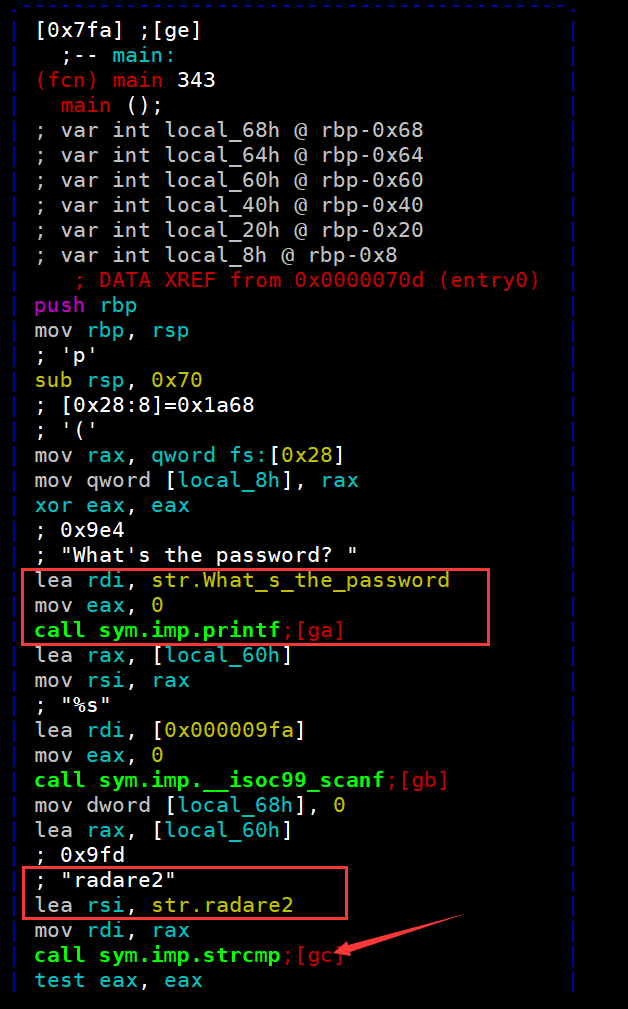
password2是将我们的输入调用atoi(将字符串转化为数字),之后跟0xf比较
那么我们的输入就是15,通过第二关
1 | # ./crackme |
接下来看看第三关,这个也是调用atoi,这次是0x539
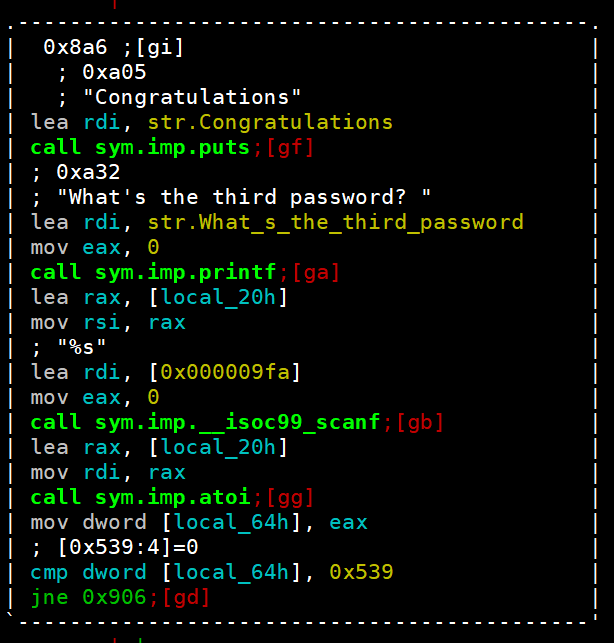
我们是学习,结果不重要,其实这还有个编码转化的工具
base64,hex,raw等都可以,不错
1 | # rax2 -h |
那么第三个password就是1337
1 | # rax2 0x539 |
那最终flag就可以出来了
1 | # ./crackme |
reference
https://medium.com/@jacob16682/reverse-engineering-using-radare2-588775ea38d5
https://medium.com/@jacob16682/reverse-engineering-with-radare2-part-2-83b71df7ffe4


