Server
下载
1 | git clone https://github.com/MozillaSecurity/FuzzManager.git |
安装依赖(注:EC2SpotManager是管理Amazon Cloud的实例的,一般用不到,用的话需要安装redis-server——apt install redis-server)
1 | cd FuzzManager |
这Server使用Django编写
Django manage.py migrate根据搜索到的文档,是创建数据库,数据表
1 | cd server |
报错解决:只要复制FTB目录到server目录里面即可
1 | root@bogon:~/FuzzManager/server# python manage.py migrate |
复制完就可以了
1 | root@bogon:~/FuzzManager/server# python manage.py migrate |
创建fuzzmanager用户
1 | root@bogon:~/FuzzManager/server# python ./manage.py createsuperuser |
获取fuzzmanager authorization token(下面的root是上面新建的用户名,这个看README的话是可以给Apache+WSGI设置虚拟主机用的,用token生成.htpasswd文件htpasswd -cb .htpasswd root 4a253efa90f514bd89ae9a86d1dc264aa3133945)
1 | root@bogon:~/FuzzManager/server# python manage.py get_auth_token root |
本地测试
1 | python manage.py runserver |
访问http://127.0.0.1:8000/即可
这个只是监听127.0.0.1,假如是服务器,还得开个反向代理或者ssh代理才能访问,所以可以下面这样
1 | python manage.py runserver 0.0.0.0:8000 |
访问了一下,发现需要在配置文件FuzzManager/server/server/settings.py中添加ALLOWED_HOSTS,就是HTTP请求的Host字段,添加本机的ip地址,假如有域名添加域名也行。
客户端
可以使用下面命令向服务器提交
1 | python Collector.py --autosubmit mybadprogram --someopt yourtest |
当然这之前得有配置文件~/.fuzzmanagerconf,下面是示例,那个sigdir是signatures存放目录,
1 | [Main] |
尝试fuzz upx,提交试试,首先配置服务器信息~/.fuzzmanagerconf
1 | [Main] |
配置程序信息upx.out.fuzzmanagerconf,放在二进制文件当前目录
1 | [Main] |
之后运行命令即可(把/usr/local/lib/python2.7/dist-packages/Collector中的Collector.py出来即可使用)
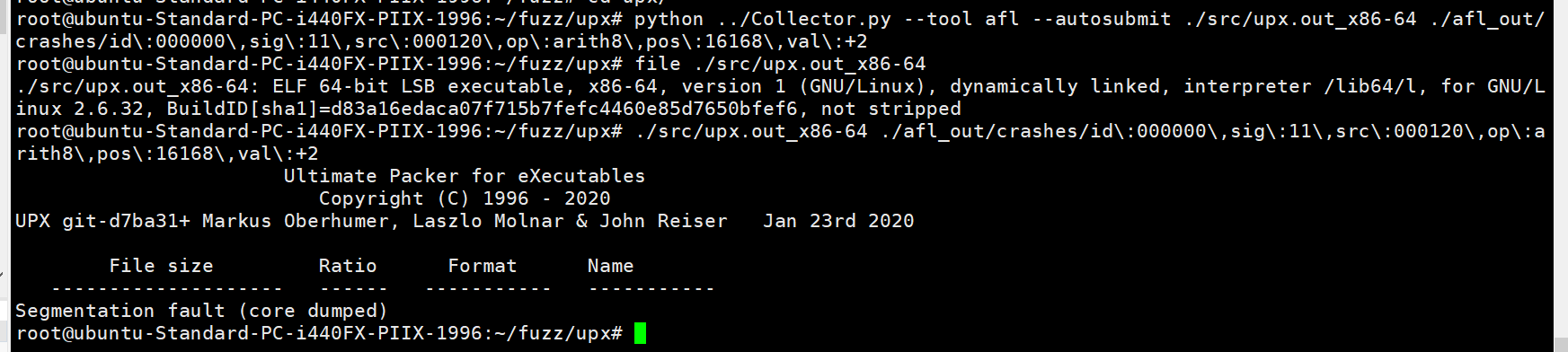
1 | python Collector.py --tool afl --autosubmit ./upx.out ./afl_out/crashes/id\:000000\,sig\:11\,src\:000120\,op\:arith8\,pos\:16168\,val\:+2 |
但是这个需要你的二进制程序是加了asan参数进行编译的,下面没有报错就是成功了
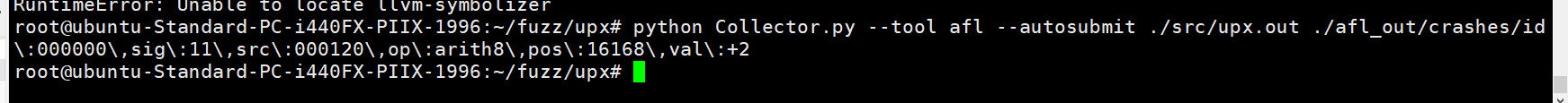
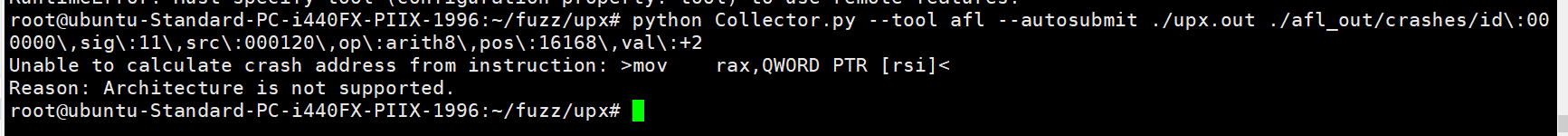
不然默认x86-64是不支持的,上传其实是上传了的,只不过没有获取到crash地址(后来发现是装了gdb插件的问题)
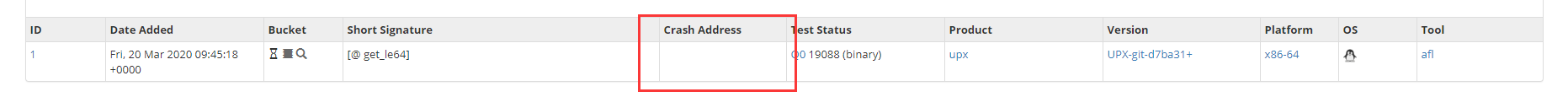
看了下源码,不加asan应该只支持x86和arm的自动提交https://github.com/MozillaSecurity/FuzzManager/blob/0ccde1820f6412da23f20da17eb3b5b9091a563e/FTB/Signatures/CrashInfo.py#L1245,需要向上翻翻看
但是后来发现是我的gdb装了peda,pwndgb插件,导致Collector.py脚本没识别出来。。。
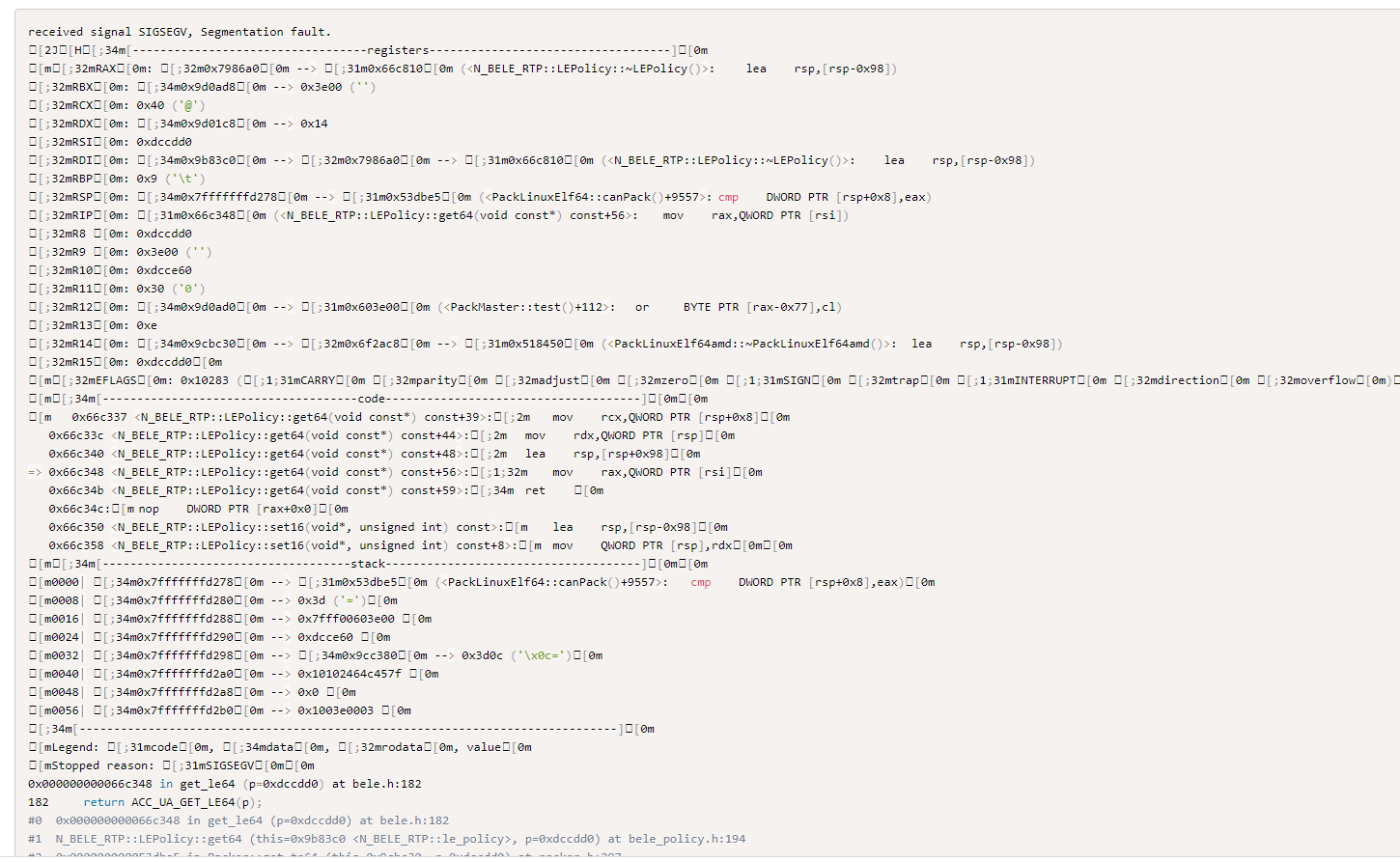
后来禁用插件后就可以了
或者自己写代码提交,下面这个来源于https://www.fuzzingbook.org/html/FuzzingInTheLarge.html
1 | from FTB.Signatures.CrashInfo import CrashInfo |
但是这个现在已经不能正常运行了,而且这个是基于python3的,我写了一个python2的版本
1 | #!/usr/bin/env python |
参考
https://github.com/MozillaSecurity/FuzzManager
https://www.fuzzingbook.org/html/FuzzingInTheLarge.html


