方式1
一个是通过抓包,一旦收到SYN,就回复一个SYN ACK
但是这个需要iptables将出去的RST ACK包给拦截掉
1 | #!/usr/bin/env python |
iptables
1 | iptables -A OUTPUT -p tcp --tcp-flags ALL RST,ACK -j DROP |
那这样nmap扫描的时候就会以为端口都开放了
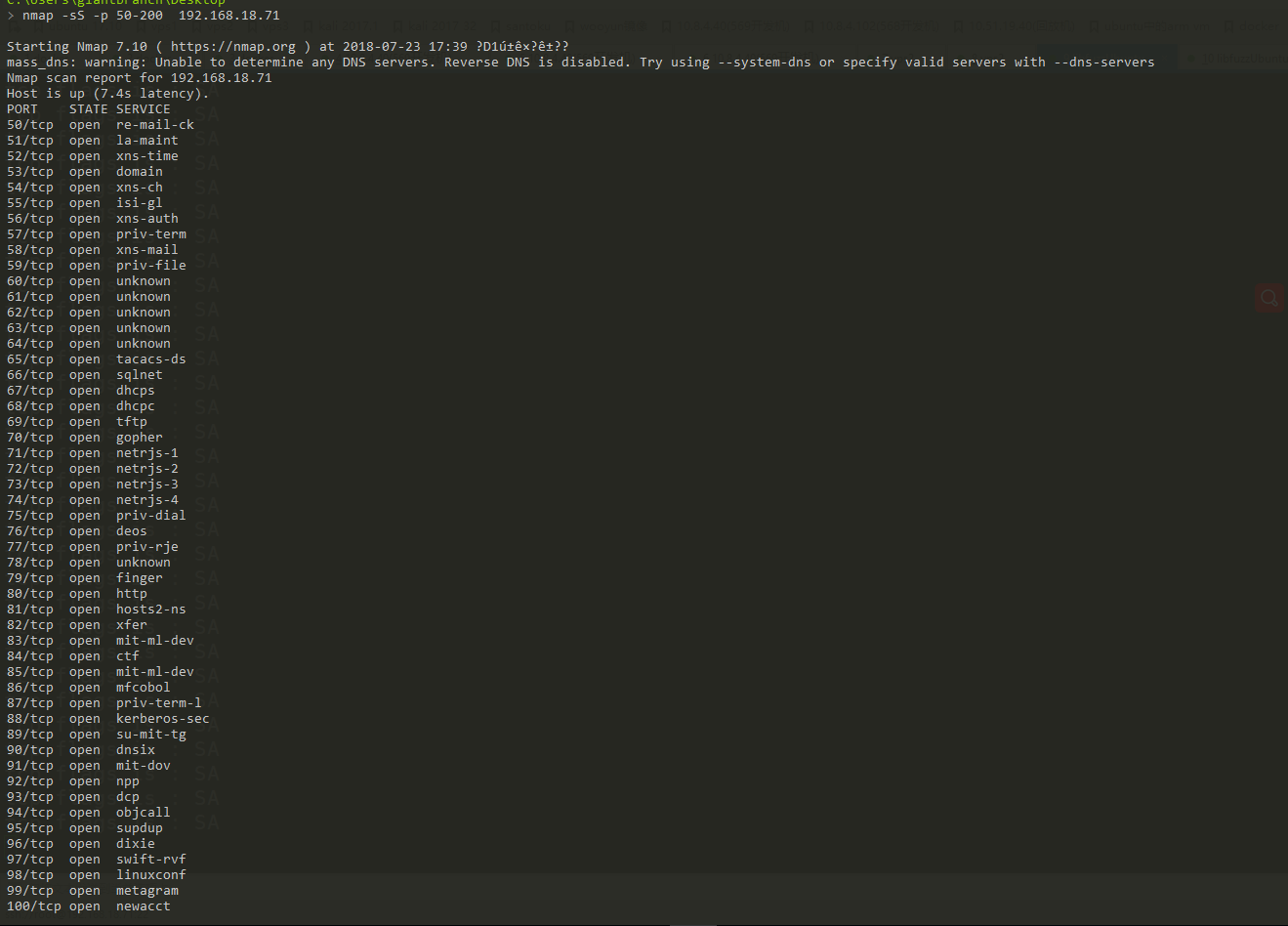
方式2
通过iptables直接做一个全端口转发,转发到你自己写的程序的端口即可
If you want to redirect all TCP and UDP traffic to Blackhole use the following command:
1 | sudo iptables -t nat -A PREROUTING -p tcp --dport 1:65535 -j REDIRECT --to-ports 5000 |
Suppose you have other services running on the Host e.g. 22, 445 and you don’t want to capture them via Blackhole,you can create multiple iptables rules:
1 | sudo iptables -t nat -A PREROUTING -p tcp --dport 1:21 -j REDIRECT --to-ports 5000 |
优缺点
抓包方式
优点:
1、实现简单
缺点:
1、有些vps,不支持伪造发送syn,ack
2、难以写交互
全端口转发到一个端口
优点:
1、真正伪造了全端口开放的假象
2、便于写对应的交互
缺点:
1、有时候获取不到目的端口
2、无其他明显的缺点
获取到的payload是空的,有可能这个端口或者协议是服务器先发送信息的
Reference
http://www.secniu.com/%E5%8D%81%E8%A1%8C%E4%BB%A3%E7%A0%81%E5%AE%9E%E7%8E%B0%E7%BD%91%E7%BB%9C%E7%9A%84%E5%85%A8%E7%AB%AF%E5%8F%A3%E7%9B%91%E5%90%AC/
https://github.com/dudeintheshell/blackhole


